Several instructors have contacted the CON IT department with questions of how Canvas sends out emails and announcements. Canvas does this differently from D2L in that each individual has control over which notifications they receive and how. Because of this, if some of your students are receiving emails when you post an announcement and others are not, this is in the control of the students– not the instructors. Below is a quick overview that you can use yourself and send out to your students so that they know where their notifications are going:
First, know that your default email is your name.#
If you would like to add an additional email for notifications, you can do this on the profile page by logging into Canvas, clicking “Account” –> “Profile” and clicking “+ Email Address” on the right side of the screen:

Now, to view and change your notification preferences, go to “Account” on the left hand side and then click “Notifications”. 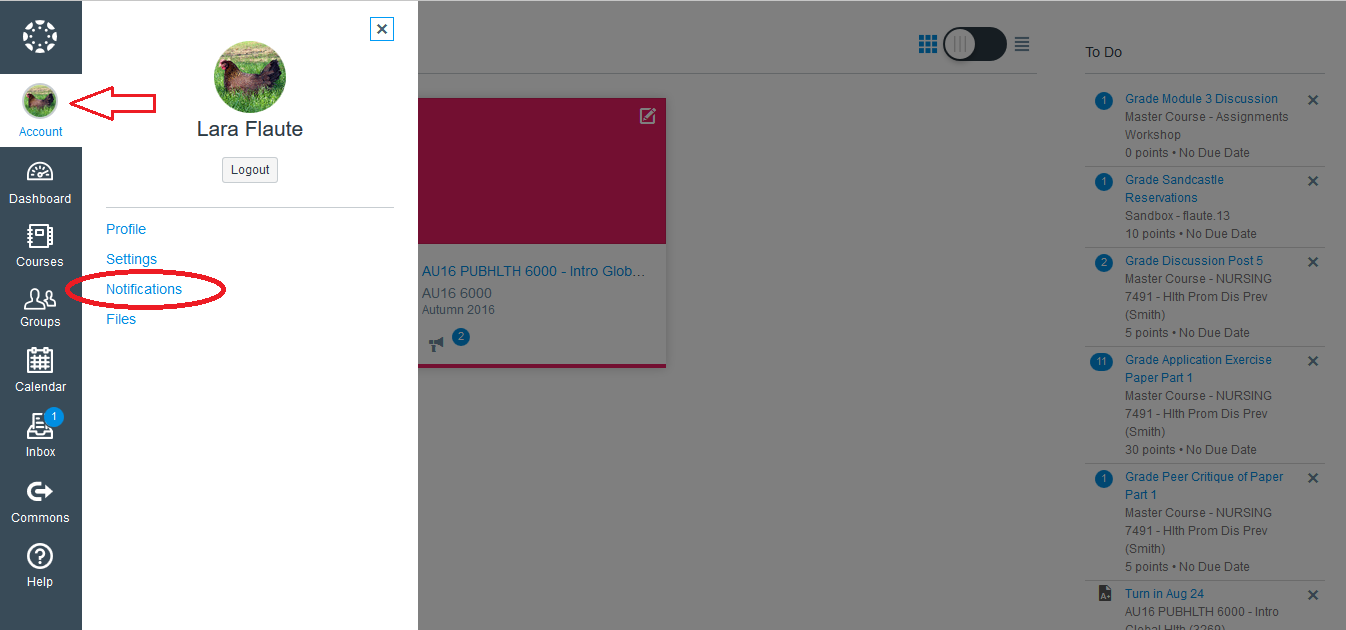
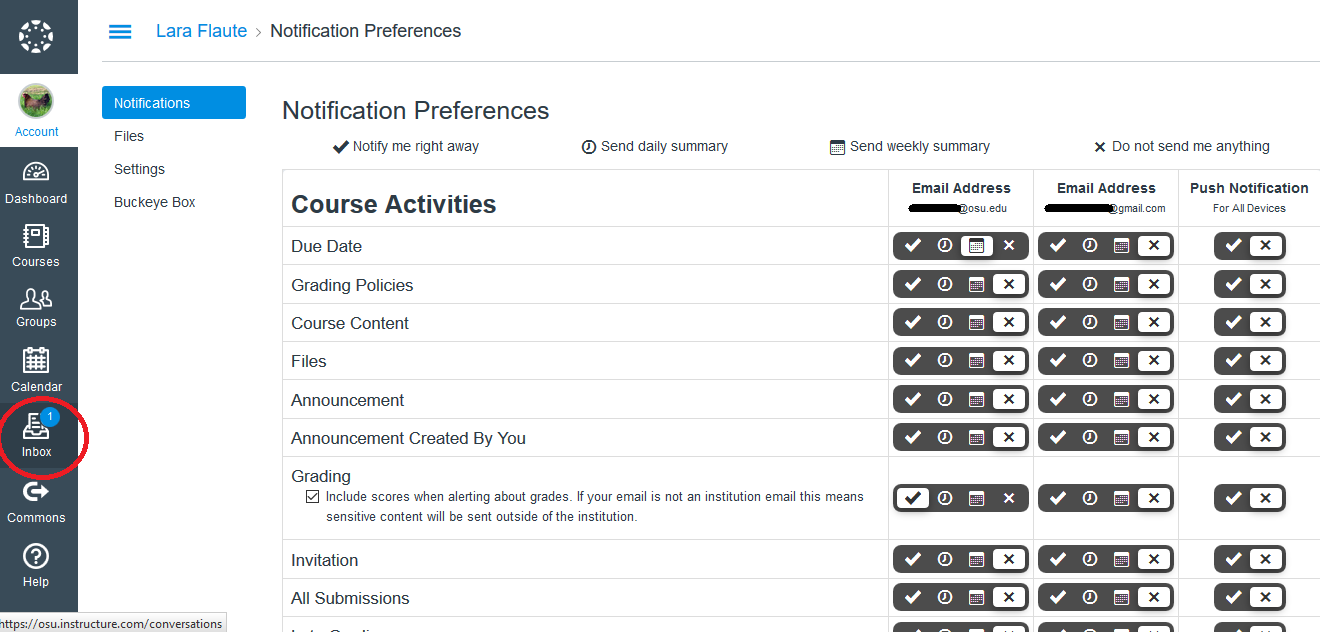
The Notification Preferences menu will open up. Along the top of the menu you will see an explanation of what each of the 4 symbols mean. There will be a column for each email address you have entered. If you have installed the Canvas app on your phone or tablet, there will also be a “Push Notification” preference column. By clicking on the corresponding symbols, you can choose whether to be notified by email for each item, and how frequently you want to receive such emails. If students are not receiving emails when you send announcements, their preferences will look like the below image.

Whether or not students receive email notifications, they can always find these notifications when they log into your classroom on Canvas.
It’s a good idea to inform your students that if they want to email their instructor from Canvas, they can do so through the “Inbox” tab on the Canvas menu (see below). The benefit of this route is that the instructor will receive the email both to their email inbox and to the Canvas inbox, and the message will inform them which course it came from.
More information can be found on the Instructure Canvas guide here.
What other burning Canvas questions do you have? Leave a comment or contact us by email to let us know!